When we talk cloud strategy, we obsess over CPUs, GPUs, and storage tiers. Yet a big silent ROI lever is the network fabric that stitches everything together.
1 | An “Open Marketplace” of Carriers—With Insider Pricing
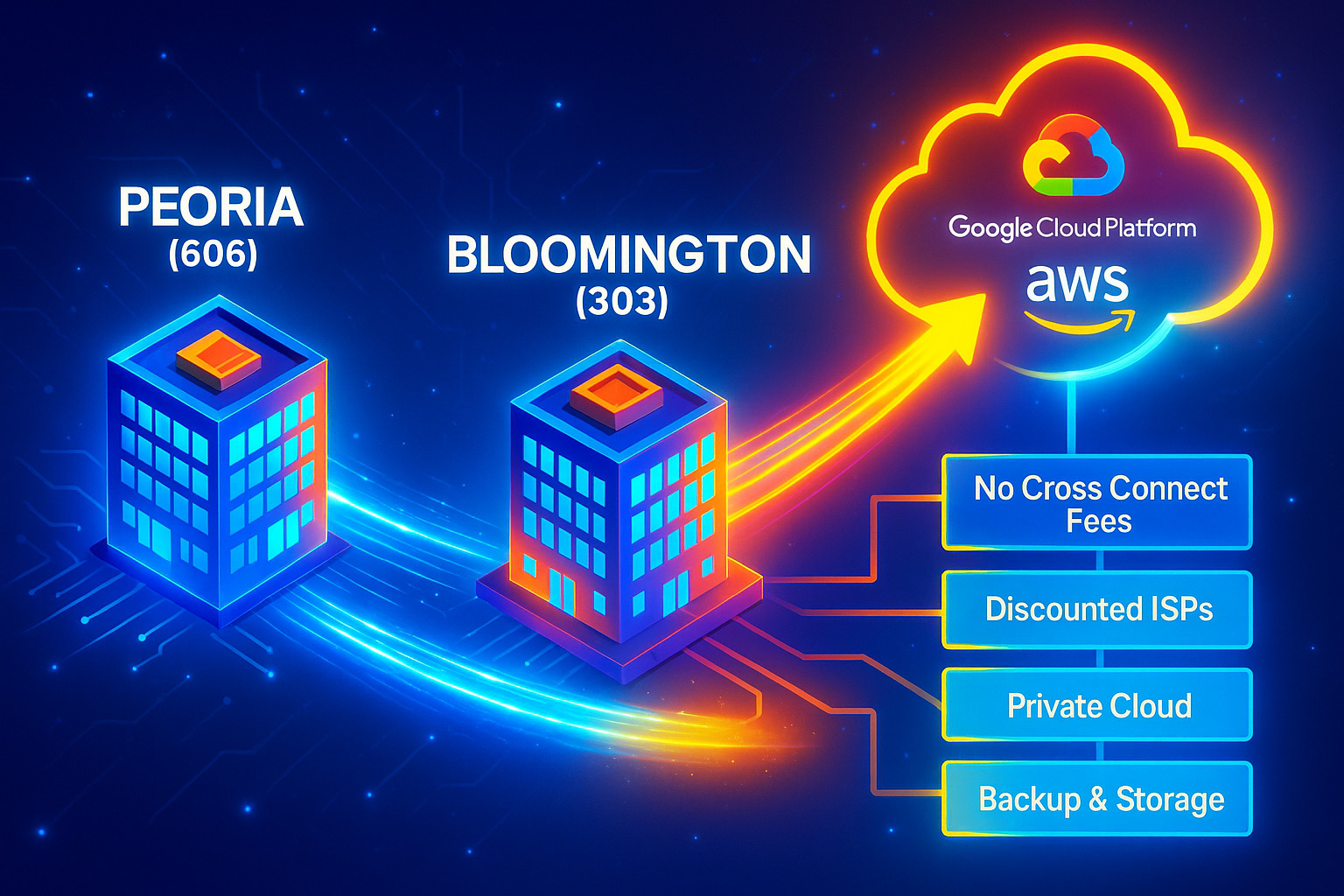
Inside our Peoria (606) and Bloomington (303) campuses, you can tap a pre-built roster of on-net carriers—Bluebird Fiber, Stratus, Comcast, Frontier, MetroNet, US Signal, Windstream, and more—without the usual cross-connect toll booth. Bulk buying means we pass along exclusive discounts you simply can’t negotiate one-to-one.
2 | Private Fast Lanes to AWS, Azure & Google
A dedicated, low-latency cloud ramp bypasses the public internet, so workloads stay fast, private, and compliant. Customers report up to 70 percent savings on egress fees while spinning up new links in minutes through a single portal.
3 | Zero-Lag Replication for True DR/BCP
Our two facilities are bridged by an ultra-low-latency Ethernet Private Line (EPL) engineered for real-time data replication. You get synchronous backup and instantaneous fail-over—capabilities that usually require metro-class budgets—at regional market pricing.
4 | Built-In SASE & SD-WAN Expertise
Planning a secure-access service edge (SASE) rollout or SD-WAN overlay? Our network engineering team designs, deploys, and manages edge-to-cloud architectures every day, letting your IT staff stay focused on apps instead of circuits.