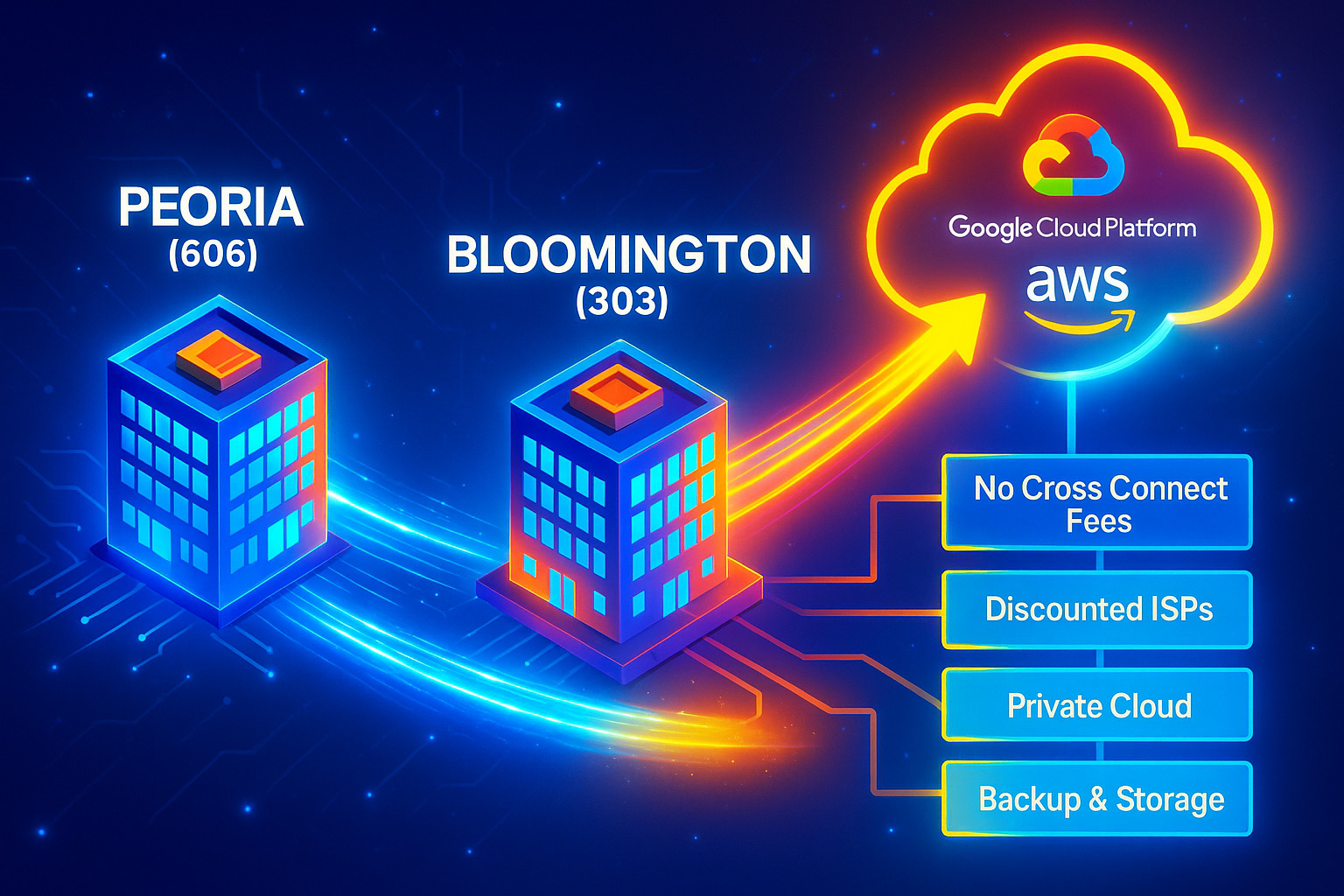
Connectivity Complements Compute
When we talk cloud strategy, we obsess over CPUs, GPUs, and storage tiers. Yet a big silent ROI lever is the network fabric that stitches everything together.

When we talk cloud strategy, we obsess over CPUs, GPUs, and storage tiers. Yet a big silent ROI lever is the network fabric that stitches everything together.

As a cybersecurity company working with regulated industries, we’ve seen just how differently businesses interpret “disaster recovery.” Some rely on a single backup drive down the hall, others deploy redundant systems across time zones. The truth is, disaster recovery (DR) isn’t one-size-fits-all—it’s about understanding your business needs and downtime tolerance, as well as crafting a strategy that’s realistic and resilient. Especially for small and mid-sized businesses (SMBs), a well-thought-out disaster recovery plan can mean the difference between business continuity and business closure.

As we move into 2025, the data center landscape is evolving rapidly, bringing exciting opportunities for businesses that rely on colocation services. Here’s a look at some key trends and how they will impact our regional Colocation data centers.

Imagine crafting a piece of ransomware, a masterpiece designed to stealthily penetrate defenses, encrypting everything in its path, rendering data inaccessible to its rightful owners. The attack begins with phishing emails, exploiting software vulnerabilities, or brute-forcing weak passwords. Once inside, the ransomware spreads like wildfire, encrypting files, databases, and backups, ensuring the victim’s desperation.

Facing an ever-changing digital terrain, companies urgently need robust IT solutions that promise not only efficiency but ironclad resilience and scalable growth as well. Among the myriad services available, colocation stands out for its multifaceted advantages. However, there’s one benefit that often goes unnoticed despite its significant impact—the strategic advantage of network connectivity diversity.

Migrating your data from on-premise servers to colocation and cloud technologies can be a daunting task. However, the overall financial savings can be extremely beneficial for businesses. By shifting from CapEx to OpEx, organizations can save a significant amount of money while still benefiting from the scalability and flexibility of cloud resources.

“Around 10% of enterprise-generated data is created and processed outside a traditional centralized data center or cloud. By 2025, Gartner predicts this figure will reach 75%.” In the world of data centers, the term “edge” is used to describe the various computing resources that are used to host applications and services outside of a centralized core. Edge computing reduces latency and improves scalability, as well as lowers the cost and complexity of managing these resources. I am personally a fan of how Gartner explains edge computing with far edge, near edge, and core.

Colocation data centers offer cost savings, scalability, security, reliability, and flexibility, allowing organizations to quickly adjust their IT infrastructure as their business needs evolve. They also provide shared infrastructure, resources, and operational expertise for reduced costs and maximum uptime and reliability. Businesses will benefit from the custom hybrid cloud designs that colocations offer at a fraction of the cost.

Do your research. Picking the right data center for your business is an important decision. When you put your data in the hands of another company, you’re putting your trust in them as well. As such, there are
The Connection That Matters Most
1003 E. Toledo Avenue
Peoria Heights, IL 61616