Boundary Protection
As part of our boundary protection strategy for your business, Pearl Technology focuses on monitoring and controlling communications through various external protection devices, such as routers, firewalls, and encryption tools. Additionally, these tools help prevent and detect malicious and unauthorized communications before they can compromise your system. Furthermore, this approach ensures a robust defense against potential threats. Consequently, you can maintain a secure and resilient network infrastructure.
Boundary Protection
E-mail Gateway
Protect your users and business from threats like malware and spam, as well as advanced threats like targeted spear phishing and ransomware. Moreover, tamper-proof archiving ensures compliance with email retention policies. In addition, strengthen your boundary protection and safeguard sensitive data with data leak prevention and encryption. Thus, you can achieve a comprehensive security posture.
Boundary Protection
Network Layers
Stay ahead of tomorrow’s threats today with the world’s first next-generation firewall (NGFW) powered by machine learning (ML). With this, you can experience complete boundary visibility, behavioral anomaly detection, risk-based policy recommendations, and built-in enforcement and prevention. Consequently, this provides a comprehensive security solution for your business. Moreover, it enhances your ability to respond to emerging threats effectively.
Read Current News From Our Team
Our expert cybersecurity team combines best-in-class technologies with decades of experience to deliver defense-in-depth strategies and custom solutions. Learn how to take a proactive approach to protecting your business.
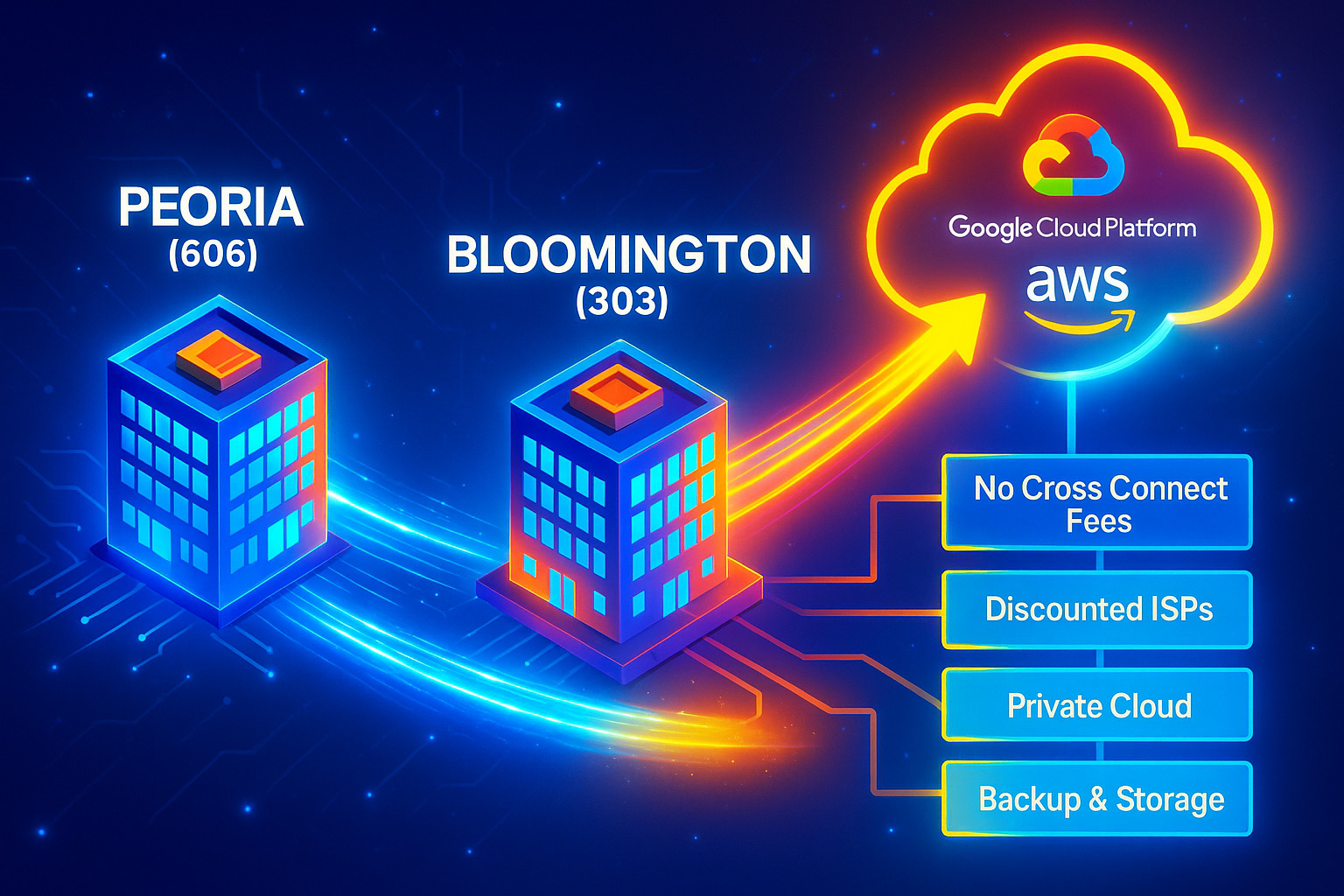
Connectivity Complements Compute
When we talk cloud strategy, we obsess over CPUs, GPUs, and storage tiers. Yet a big silent ROI lever is the network fabric that stitches everything together.

One Disaster Recovery Tip That Could Save Your Business
Imagine crafting a piece of ransomware, a masterpiece designed to stealthily penetrate defenses, encrypting everything in its path, rendering data inaccessible to its rightful owners. The attack begins with phishing emails, exploiting software vulnerabilities, or brute-forcing weak passwords. Once inside,

Tips to Help Protect Your Data
Given the recent AT&T data breach, Anthony Mini recommends the following:
1. Monitor your accounts with identity protection services.
2. Check the status of your e-mail accounts that have been exposed to other breaches using the website: https://haveibeenpwned.com/.<br