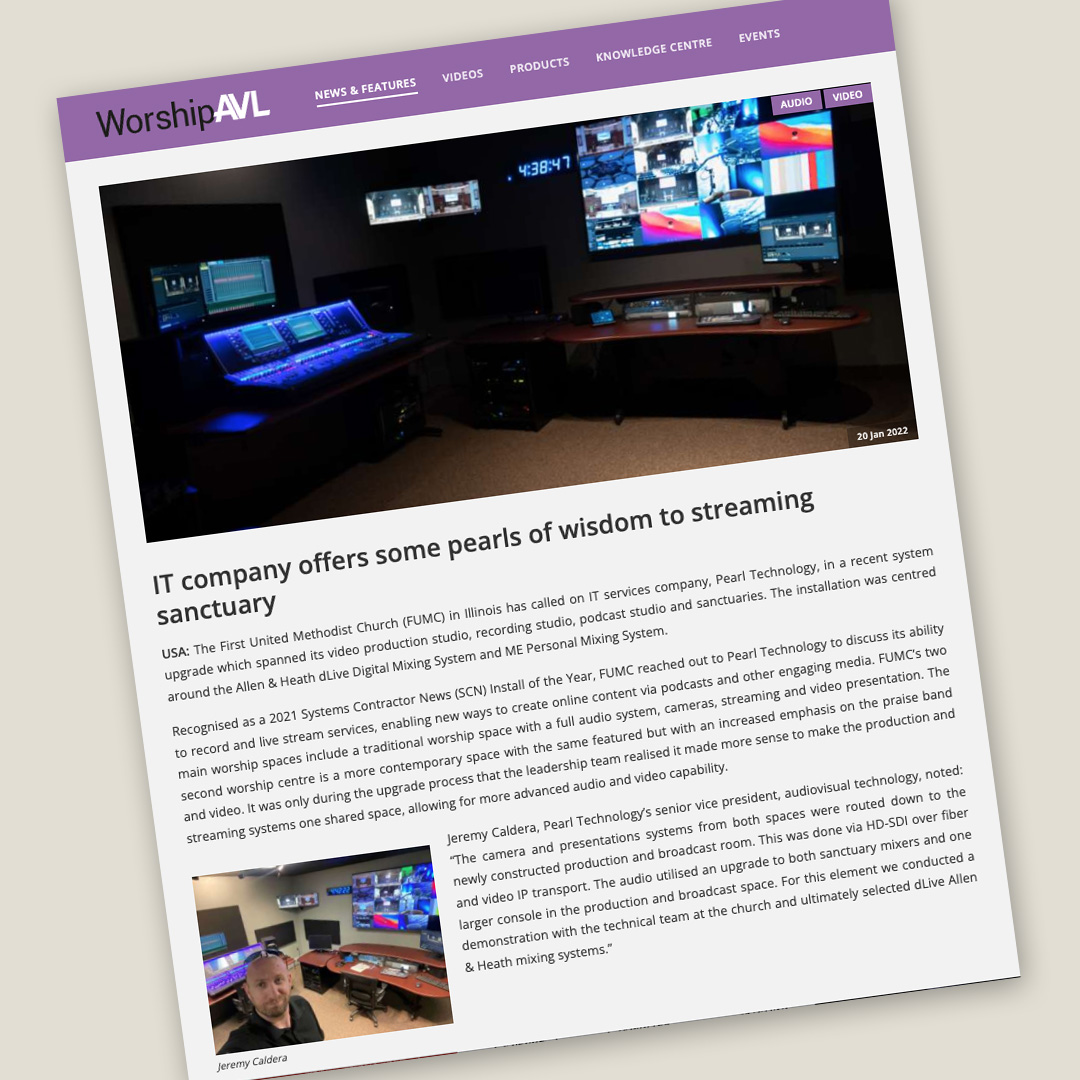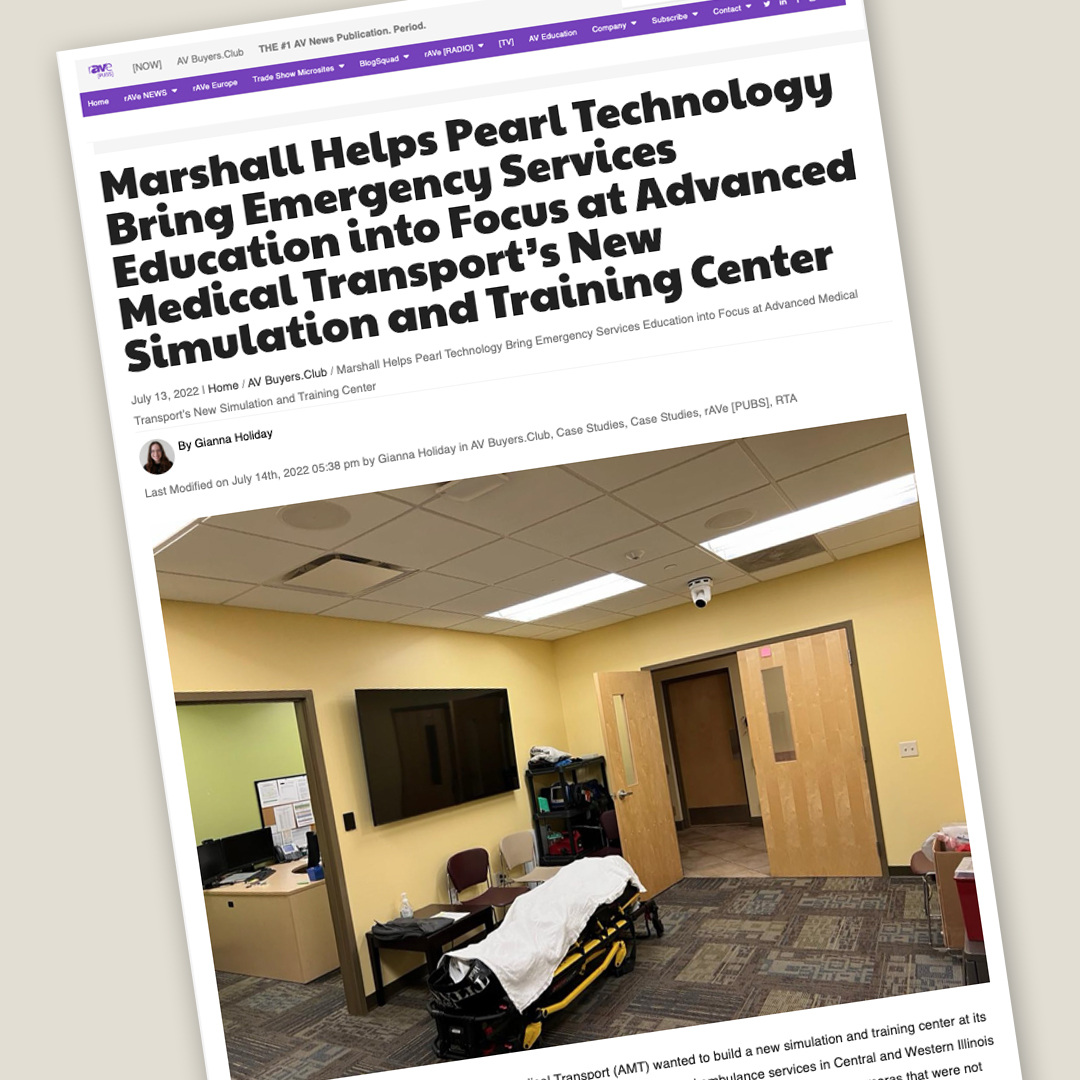
Pearl Technology Recognized for Work on AMT’s Training Center
When Advanced Medical Transport (AMT) needed a new simulation and training center, they worked with Pearl Technology to provide state-of-the-art audiovisual components. For the solution, our team worked with Marshall Electronics to utilize innovative equipment to achieve AMT’s